Cyber Intelligence
It is the acquisition and analysis of information to identify, track, and predict the capabilities, intentions, and cyber activities that support decision-making.

With the rise of cyber threats, it is crucial to have tools and strategies to protect digital assets. Cyber intelligence plays a fundamental role in this context, providing proactive and reactive defense against cyberattacks.

Cyber intelligence is an advanced service that implements proactive strategies for the prevention, detection, and investigation of security incidents.
At Silent4Business, our cyber intelligence services are developed through a specialized team known as CSIRT.




With the implementation of cyber intelligence, we provide robust defense tailored to the specific needs of each organization.





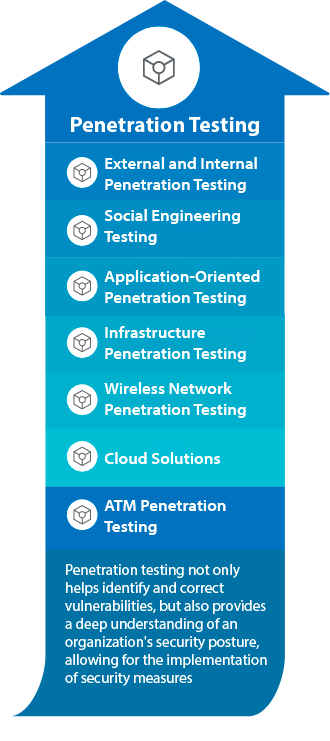
Penetration testing consists of simulating a cyberattack to identify vulnerabilities in a computer system and fix them before they can be exploited by cybercriminals. These tests provide a detailed view of system weaknesses, allowing organizations to take preventive and corrective actions.
Benefits of our penetration testing: Planning and reconnaissance: Identifying the goals and scope of the pentest, as well as gathering relevant information.
Scanning: Analyzing the network and systems to identify potential entry points. Gaining access: Attempting to exploit vulnerabilities to access systems.
Maintaining access: Estimating the ability of cybercriminals to maintain access to compromised systems.
Analysis and reporting: Detailed documentation of identified vulnerabilities and recommendations for mitigating them.
We have the following tests available to help you achieve your goals.
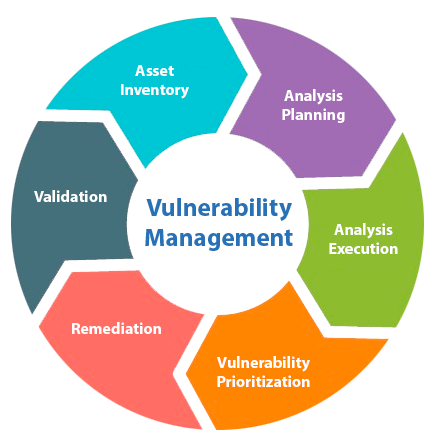
Vulnerability analysis is a critical process that involves identifying and prioritizing weaknesses in applications and systems.
Vulnerability identification: Using automated and manual tools to detect weaknesses in systems and applications.
Risk assessment: Analyzing the severity of vulnerabilities and their potential impact on the organization.
Prioritizing vulnerabilities: Categorizing vulnerabilities based on their risk and urgency for correction.
Recommending solutions: Suggesting actions to mitigate or eliminate identified vulnerabilities.
Vulnerability analysis is an integral part of a cybersecurity strategy, as it enables organizations to identify and address weaknesses before they
Our forensic analysis in cybersecurity allows you to search for and recover hidden, damaged, or deleted data, providing you with a detailed understanding of security incidents and helping to identify the root cause of attacks.
Data collection: Gathering digital evidence from compromised systems. Evidence preservation: Ensuring that the collected data is not altered during the analysis process.
Analyzing the evidence: Using specialized tools to examine the digital evidence and uncover how the incident occurred.
Documentation and reporting: Creating detailed reports describing the findings and providing recommendations to prevent future incidents.
We help your company adapt and respond efficiently to business and security challenges, strengthening its resilience and competitiveness.
- Constant and proactive monitoring: Cyber intelligence enables continuous surveillance to identify and mitigate threats before they cause damage.
- Advanced prevention and detection: Uses artificial intelligence and machine learning to anticipate attacks and protect systems more effectively.
- Rapid analysis and response: Provides forensic investigation and immediate response to incidents to minimize the impact on the organization.