Technology Solution
At Silent4Business, we specialize in providing technology solutions tailored to the cybersecurity needs of your company.
Our agnostic approach allows us to work with the best tools available in the market, without being limited to a single brand or provider. This ensures the protection of your digital infrastructure against the most advanced cyber threats.
These are just some of the solutions we can integrate:Advanced solutions are essential to protect corporate environments from the most complex and targeted attacks. At Silent4Business, we offer a set of technologies designed to safeguard data integrity, optimize system access, and strengthen security at all levels.
Crucial to prevent data leaks that could compromise the security of your organization.
Simplifies credential management, allowing users to access multiple applications with a single authentication.

Controls who has access to what within the organization and minimizes the risks of unauthorized access to sensitive data.
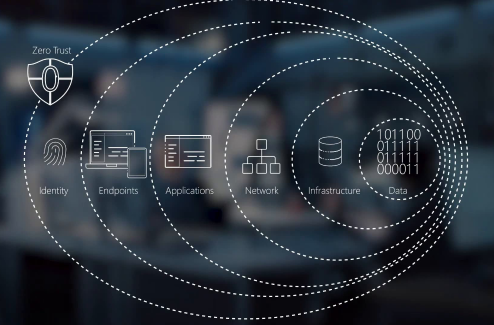
We adopt the Zero Trust approach, where no user or device is trusted by default, even if they are inside the corporate network.
In today’s landscape, companies constantly face attempts of cyberattacks aimed at breaching their systems. Perimeter protection is your first line of defense to block these threats before they reach the core of your infrastructure.

Traditional firewalls have evolved into smarter solutions that not only block unauthorized traffic but also inspect and analyze suspicious behavior.
To ensure optimal system performance, our load balancers efficiently distribute traffic, while content filtering prevents malicious or inappropriate content from accessing the corporate network.


We provide specialized solutions to mitigate these attacks before they cause service disruptions. Additionally, our protection against advanced attacks prevents exploitation attempts of vulnerabilities and targeted attacks.
Using robust antivirus is essential to protect all endpoints within an organization. Combined with Multi-Factor Authentication, we ensure that only authorized users can access critical systems, even if their credentials are compromised.

Monitors and correlates security events in real time, making it easier to identify potential threats before they become a bigger issue.

Protects web applications from common attacks like SQL Injection and Cross-Site Scripting (XSS), while the Database Firewall ensures that critical stored data is protected from unauthorized access and manipulation.
Prevents attackers from using DNS to launch attacks against the network, while Host IPS monitors and protects servers from suspicious activities, ensuring that vulnerabilities cannot be exploited.


Monitors and correlates security events in real time, making it easier to identify potential threats before they become a bigger issue.