SOC / NOC
Designed to protect the most important elements of a public or private institution: information and its people, with the main objective of monitoring security systems to keep them safe from threats or unnecessary risks.
The Security Operations Centers (SOC) and Network Operations Centers (NOC) play important roles in ensuring and optimizing the IT infrastructure of organizations. Although both centers work for the proper functioning of companies, their functions and objectives are different.

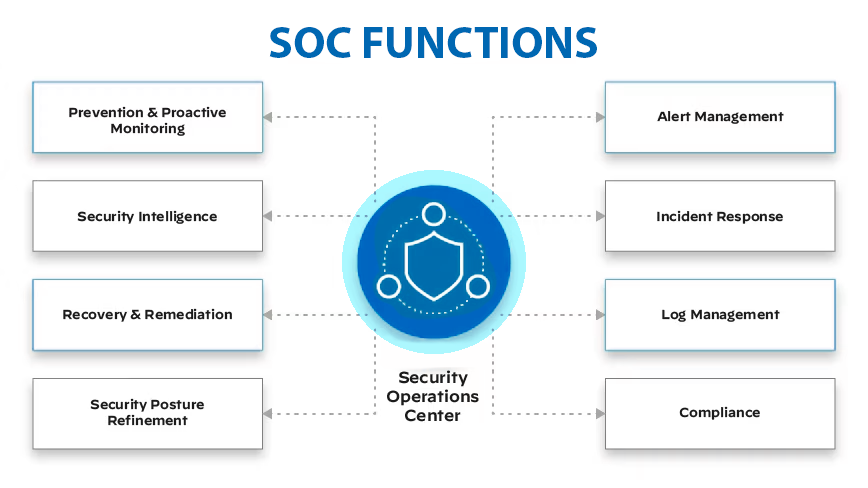
· Managed security for multi-brand solutions: A set of solutions that includes continuous monitoring, detection, and response.
· Hybrid correlation: This technique enables the detection of suspicious and anomalous activity by combining data from various sources to identify threat patterns.
· Specialized support: SOC analysts provide expert technical support for security solutions, helping resolve complex problems efficiently.
· Security reports: Detailed reports on the security status and detected threats help organizations better understand their security posture and make informed decisions.
Essentially, the SOC provides companies with an additional layer of protection, ensuring that threats are detected and managed before they can cause significant damage.

· Network mapping: Creating and maintaining a detailed map of the network infrastructure, identifying all components and connections.
· Infrastructure provisioning: Managing the installation, configuration, and maintenance of network equipment and related services.
· Performance monitoring: Constantly monitoring network performance to identify and resolve issues before they impact end users.
· Application monitoring: Ensuring that critical applications function correctly and meet user needs.
· Monitoring reports: Providing detailed reports on network status and performance, enabling organizations to make decisions based on accurate data.
The NOC ensures that the network infrastructure is operational and performing at optimal levels, enabling the company to maintain productivity and efficiency.
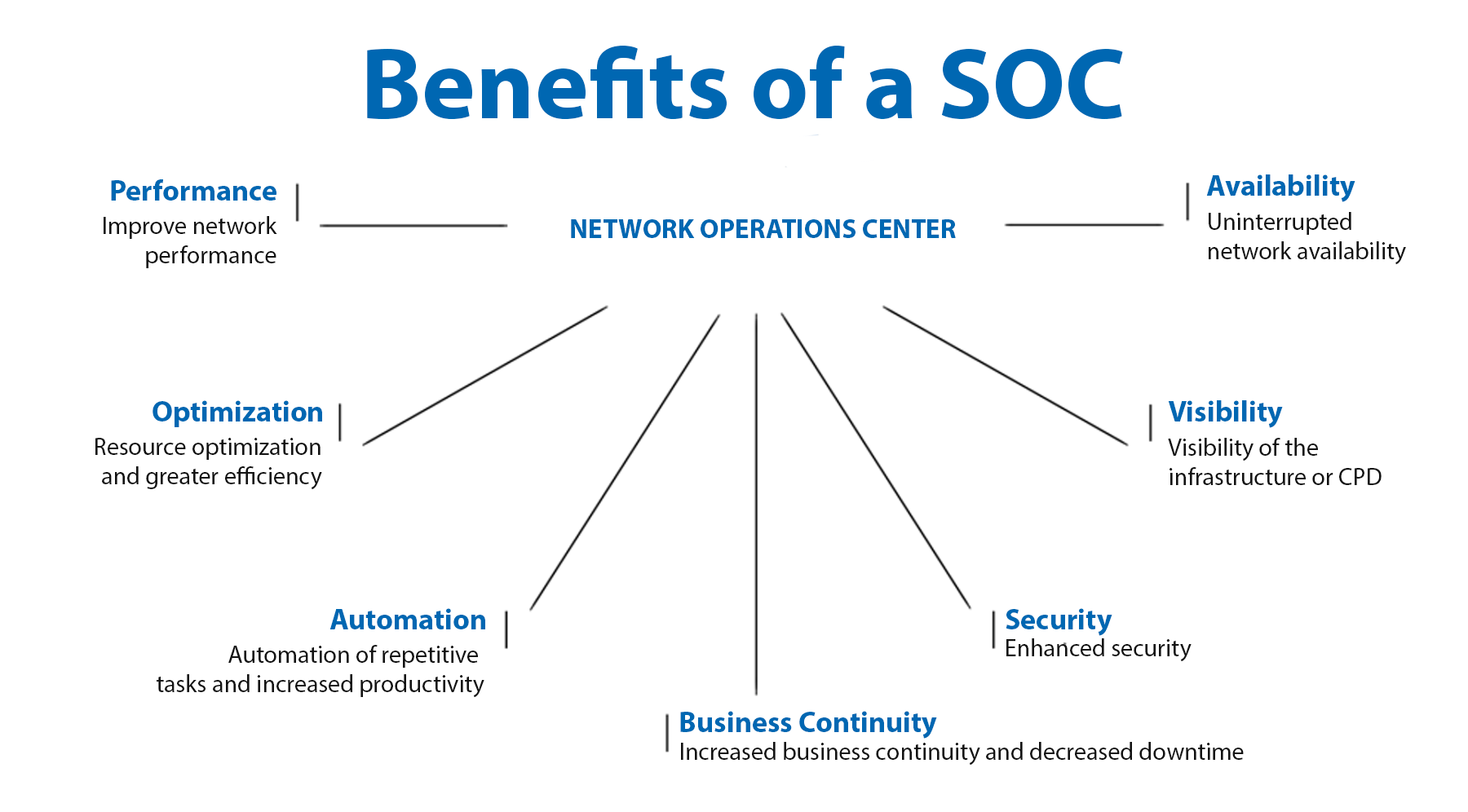

Having a SOC/NOC is crucial to maintaining the security and operability of your company's IT infrastructure:
· Comprehensive security: While the NOC ensures the network operates correctly, the SOC protects against external and internal threats. Together, they provide complete IT infrastructure coverage.
· Rapid incident response: With a NOC, any network issue is identified and resolved quickly. With a SOC, any security threat is detected and effectively managed. This combination ensures that any problem, whether technical or security-related, is handled with speed and accuracy.
· Resource optimization: By having both centers, an organization can optimize its IT resources, ensuring both operability and security are efficiently managed.